During 30 hours of Microsoft Intune training, you will learn about mobile device management (MDM) and mobile application management (MAM). Learners will master skills to manage updates, enrol devices and profiles, and control your organization’s devices like tablets, mobiles, and laptops. Every concept follows a practical approach through step-by-step instructions and hands-on use cases to create compliance policy, deep link apps, standard device settings, device alerts, reporting, and Azure Active Directory.
Microsoft Intune Course Content
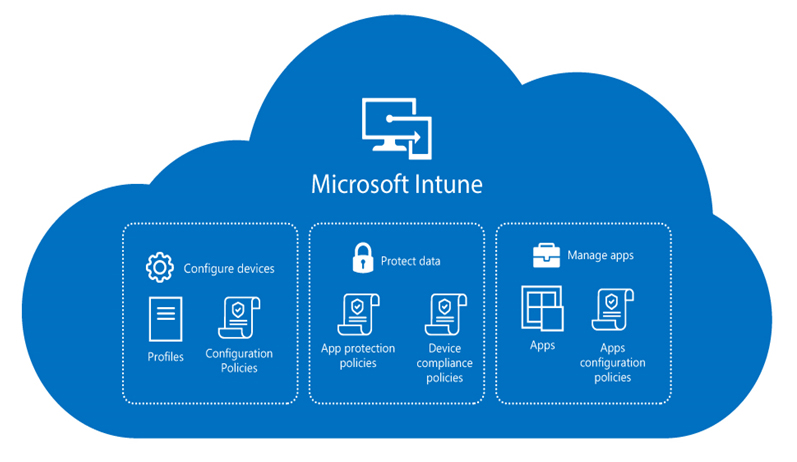
Microsoft Intune course curriculum covers all the topics needed to control and manage an organization’s devices, that include mobile phones, tablets, and laptops. Intune training makes you an expert at MDM and MAM.
Module1: Plan for the Microsoft Intune
- Planning Product and License Capabilities and Requirements
- Identity Strategy – Groups/Users
- Mobile device management strategy Hybrid vs. Cloud
- Physical Device Notions CYOD/BYOD
- License Assignment
- Utilization of Intune Portals
Module2: Compliance
- Compliance in Microsoft Intune
- Creating the Compliance Policy
- Utilizing the multiple compliance policies
Module3: Handling Updates and Applications
- Mobile Application Management without enrollment on Android and iOS devices.
- Sideload and Deeplink Apps
- Using the Intune Software Publisher
Module4: Configuration
- Android
- Configuration in Intune
- Android for Work
- Windows and Mac OS X
- Software
- Common Device Settings
- Computer Management
Module5: Enroll Alerts, Devices, Reporting, and Troubleshooting
- Alerts Overview
- IOS Certificates
- Enrolling Devices
- Device and Policy Alerts
- Reporting and Troubleshooting
- Service Alerts
Module6: Reporting and Monitoring through Microsoft Intune
- Reporting and Monitoring through Microsoft Intune
Module7: Intune as an Integral Part of Enterprise Mobility and Security Product Suite
- Azure Information Protection
- Azure Active Directory
- Microsoft Cloud App Security
- Microsoft Identity Manager
- Microsoft Advanced Threat Analytics

